Handle: Data Security
question Questionsobjectives Objectives
- What measures are important to keep your data safe and secure?
- Understand different ways data breaches can happen so you know how to avoid this;
- Understand different ways to achieve data security and reasons for access restrictions;
- Link situations to different legal contracts that arrange access and security;
- Recognise indirectly identifiable data;
- Store and manage privacy-sensitive data;
- Apply the gained knowledge about data security to your own research data and write the data security section for your data management plan.
time Time estimation: 40 minutes
Introduction to data security
By now you know more about how to manage your data collection, how to organise and document your research data and where and how to store your data.
Now we will take you into the world of keeping data safe and secure.
Loss of data, loss of academic career
The loss of scientific data can have a devastating impact on careers. Imagine that you loose all of the research data you’ve been diligently collecting for four years. Now imagine the knock-on effect: you won’t get the PhD you’ve been working towards, affecting your future career. This nightmare happened to Billy Hinchen, a biologist at Cambridge University. Listen to his story.
Data breaches
There are several examples of (mainly online) data storage going wrong, leading to leaks of sensitive and personal information.
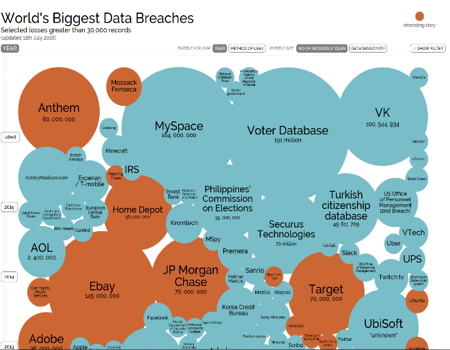
The picture below shows the biggest cases of data breaches in the past 10 years. They involve some well-known, highly regarded and trusted companies as well as some practices from the academic world. Read about the story
Prevent unauthorised access
Data security may be needed to protect intellectual property rights, commercial interests, or to keep personal or sensitive information safe. Data security involves security of data files, computer system security and physical data security. All three need to be considered to ensure the security of your data files and to prevent unauthorised access, changes, disclosure or even destruction. Data security arrangements need to be proportionate to the nature of the data and the risks involved. Attention to security is also needed when data are to be destroyed. If data destruction is in order, you need to make sure that the destruction process is irreversible.
Learn about different measures depending on the kind of security you need.
Security of data files
The information in data files can be protected by:
- Controlling access to restricted materials with encryption. By coding your data, your files will become unreadable to anyone who does not have the correct encryption key. You may code an individual file, but also (part of) a hard disk or USB stick
- Procedural arrangements like imposing non-disclosure agreements for managers or users of confidential data
- Not sending personal or confidential data via email or through File Transfer Protocol (FTP), but rather by transmitting it as encrypted data e.g. FileSender
- Destroying data in a consistent and reliable manner when needed
- Authorisation and authentication: for personal data you have to give very selective access rights to specified individuals.
Computer security systems
The computer you use to consult, process and store your data, must be secured:
- Use a firewall
- Install anti-virus software
- Install updates for your operating system and software
- Only use secured wireless networks
- Use passwords and do not share them with anyone. Do not use passwords on your UU computer only, but also on your laptop or home computer. If necessary, secure individual files with a password.
- Encrypt your devices (laptop, smartphone, USB stick/disk).
Physical data security
With a number of simple measures, you can ensure the physical security of your research data:
- Lock your computer when leaving it for just a moment (Windows key + L)
- Lock your door if you are not in your room
- Keep an eye on your laptop
- Transport your USB stick or external hard disk in such a way that you cannot lose it
- Keep non-digital material which should not be seen by others, in a locked cupboard or drawer.
Data classification
TODO: what to do with classified data
Data that contain personal information
These data should be treated with higher levels of security than data which do not. You will learn more about privacy-sensitive data in the e-module.
What is your experience with unauthorised access to your research data?
TODO: implementation form widget
We are interested to know if you have ever experienced unauthorized access to any of your research data. When you give your reply, we will show you an overview with the responses of other researchers in this course. All responses will be processed anonymously.
[(1)] No, I am sure about that [(2)] Not that I am aware of [(3)] Yes, without much consequences [(0)] Yes, with severe consequences
Legal agreements and contracts
Often other people are required to handle your data, or you might be the person that handles other people’s data.
To arrange the security of the research data you work with, in many cases you have to make a (legal) agreement with other people involved. These agreements will make explicit permitted uses, retention time, and agreed upon security measures. Find out what legal contracts you can use by studying the figure below. TODO: Visit the Guide ‘Legal instruments and agreements’ for more information
For tailored advice and templates, contact Legal Affairs via your faculty Research Support Officer (RSO)
TODO: add link
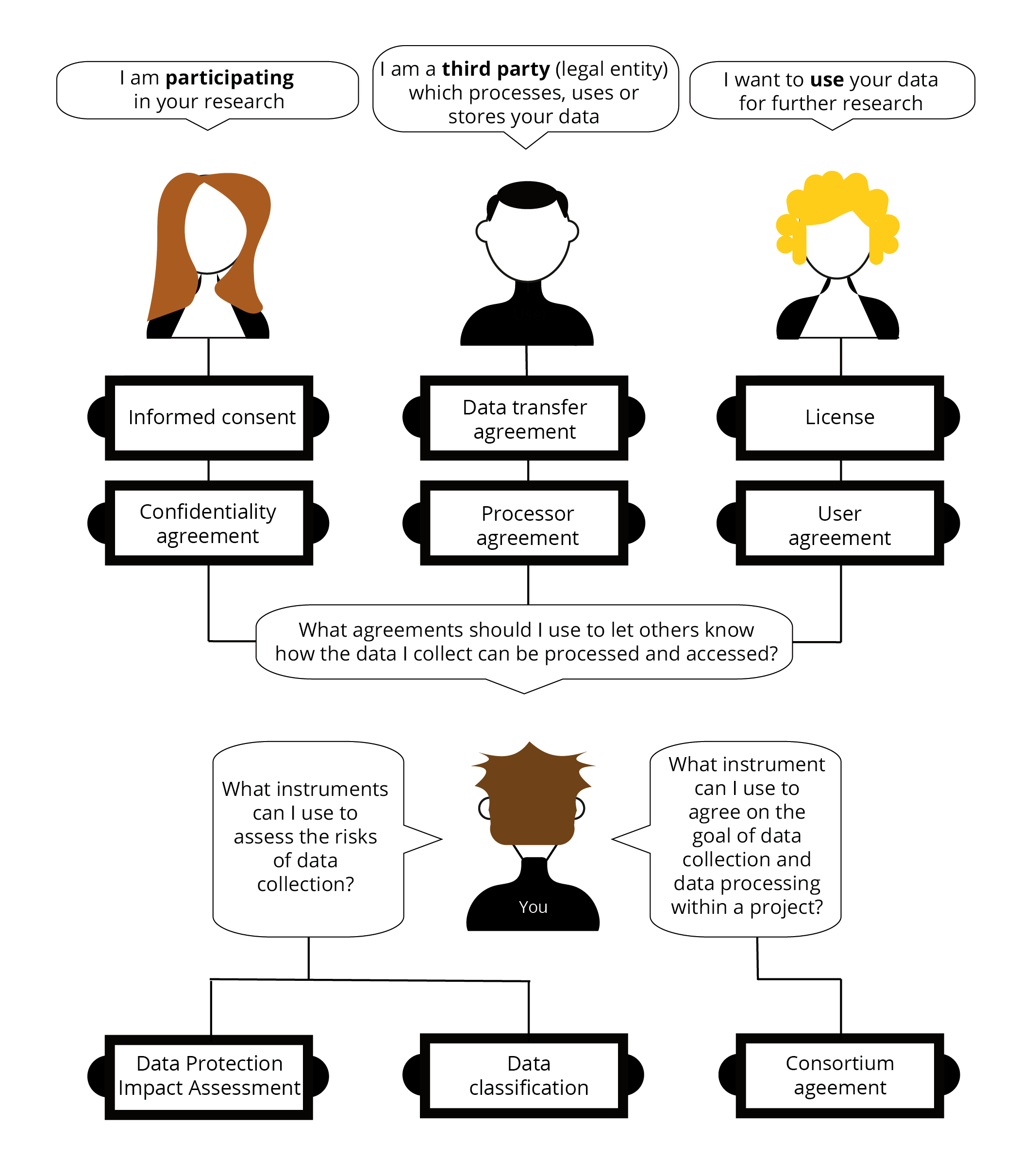
When to use which legal contract?
You have been acquainted with the different flavors of legal agreements. Is it clear to you when you need which agreement? Please answer the following questions by choosing the right kind of agreement.
TODO: add quiz or H5P quiz
Privacy-sensitive data

Privacy in a nutshell
Privacy is a fundamental right. With regards to privacy, we all have two perspectives:
- How is your privacy protected?
- How can we, as a researcher, protect the privacy of the people involved in our research (the data subjects)?
TODO: add link to document and image screenshot

Six principles from the European General Data Protection Regulation 1/2
The European General Data Protection Regulation (GDPR) outlines how we should work with privacy-sensitive data.
TODO: create working infographics with images see http://gdprcoalition.ie/infographics
Six principles from the European General Data Protection Regulation 2/2
According to the GDPR processing of personal data must be done according to 6 principles.
TODO: create HP5 document
The GDPR outlines six data protection principles you must comply with when processing personal data. These principles relate to:
- Lawfulness, fairness and transparency - you must process personal data lawfully, fairly and in a transparent manner in relation to the data subject.
- Purpose limitation - you must only collect personal data for a specific, explicit and legitimate purpose. You must clearly state what this purpose is, and only collect data for as long as necessary to complete that purpose.
- Data minimisation - you must ensure that personal data you process is adequate, relevant and limited to what is necessary in relation to your processing purpose.
- Accuracy - you must take every reasonable step to update or remove data that is inaccurate or incomplete. Individuals have the right to request that you erase or rectify erroneous data that relates to them, and you must do so within a month.
- Storage limitation - You must delete personal data when you no longer need it. The timescales in most cases aren’t set. They will depend on your business’ circumstances and the reasons why you collect this data.
- Integrity and confidentiality - You must keep personal data safe and protected against unauthorised or unlawful processing and against accidental loss, destruction or damage, using appropriate technical or organisational measures.
Privacy by design
To comply with the six principles from the GDPR, you can implement privacy by design. This means that you design a data management plan with measures on both IT and procedural level.
Which data breach is breached?
Can you recognise the principles that are breached in the different ways personal data is processed?
TODO: H5P quiz 7 cases
Storing personal data 1/2
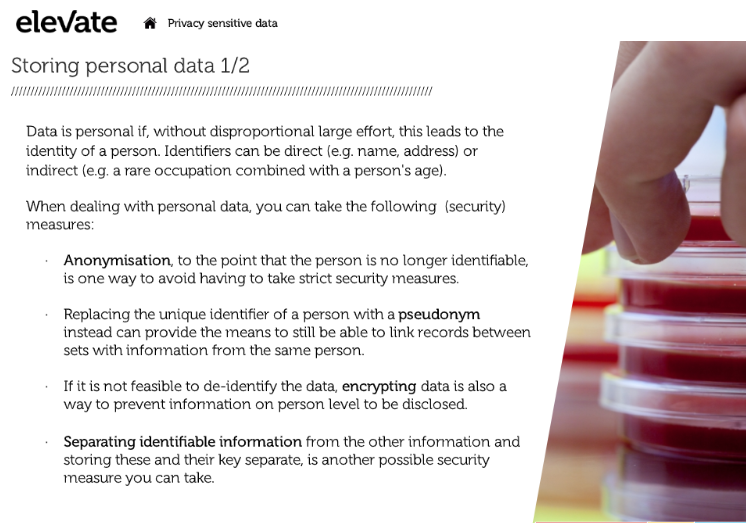
Storing personal data 2/2
Only if the access can be unambiguously be restricted to authorised persons, can data be stored without such measures.
Should you want an elaborate visualisation of what is considered identifiable data, check out the information sheet at the Future Privacy Forum.
Download the visual guide to practical data de-identification
Can you recognize identifiable data?
question Can you recognize identifiable data?
- a collection of GPS data of daily routines
- a list of households sizes associated with number of pets
- MRI scans without identifying metadata.
- audio recordings with no metadata and no names of the recorded persons
- transcripts of interviews without any directly identifying information
- a list of gender and grades for a de-identified course
Check the answers.
Answer 1,3, and 4 are correct!
GPS data holds information on where people go. In a daily routine, the track ends at a particular location which is likely the home of the subject. AN MRI scan from the profile of the head can be identifiable. Audio recordings can be identifiable from the tone of the voice. A list of surnames in itself is not identifying nor personal information.
Access to privacy-sensitive data
If and how you can make personal data available, depends n the level of sensitivity of your data. The more sensitive, the more restrictions and safeguards need to be put in place to make sure the data does not fall into the hands of unauthorised persons both during and after research.
To determine where the privacy risks lie for your data you will have to do a Data Privacy Impact Assessment (DPIA).
For more information:
TODO: link to: https://www.uu.nl/en/research/research-data-management/guides/handling-personal-data
Towards the data subjects, you need to be transparent regarding the possible reuse, or retaining of the data for verification requirements, and get their prior consent.
Cases on how to make personal data accessible
Case 1: YOUth cohort study
YOUTH COHORT STUDY YOUth (Youth Of Utrecht) is a large-scale, longitudinal cohort following children in their development from pregnancy until early adulthood.
A total of 6,000 babies and children from Utrecht and its surrounding areas will be included in two different age groups and followed at regular intervals.
The YOUth data enables researchers to look for answers to all sorts of scientific questions on child development. A few examples of YOUth data: human bodily material, hours of videos, MRI images, questionnaires, ultrasounds and IQ scores. YOUth encourages and facilitates data sharing. It is one of the leading human cohorts in FAIR and open data in the Netherlands.
More information at: https://www.uu.nl/en/research/youth-cohort-study
Case 2: TODO: other example from Wings?
An introduction to informed consent
In the module ‘Legal agreements and contracts’ you learned about informed consent. Informed consent is very important when working with data which is in any way related to people.
TODO: add graphics on informed consent
One thing to arrange in your informed consent is the possibility for future use, for verification or reuse. In your informed consent, it is important to be clear on future use of data.
Informed consent for data sharing
One thing to arrange and to be crystal clear about in your informed consent is the possibility for future use of your data, for verification or reuse.
question Question
Check the sentences that do permit data sharing if used as a single statement.
- Any personal information that reasonably could identify you will be removed or changed before files are shared with other researchers or results are made public.
- Other genuine researchers (may) have acces to tis data only if they agree to preserve the confidentiality on the information as requested in this form.
- Any data that could identify you will be accessible only to the researchers responsible for performing this study.
- All personally identifying information collected about you will be destroyed after the study.
Check the answers.
Answer 1 and 2 are both correct!
Sharing of research data that relates to people can often be achieved using a combination of obtaining consent, anonymizing data and regulating data access. If the statement towards the data only mentions the current study, sharing is not explicitly possible. You should add some sentence to make it clear to participants that the data could be used for further research, deidentified where possible, or identifiable with enough safeguards and security measures, if it is not.
Write your data management plan for your data security
Go to DMPonline and open your draft data management plan created in the Introduction.
You have now completed the module on data security. You should be able to complete the following questions in the section ‘Data security’:
- Will you use or collect any confidential or privacy-sensitive data?
- What measures will you take to ensure the security of any confidential or privacy-sensitive data?
- What measures will you take to comply with security requirements and mitigate risks? To whom will access be granted/restricted?
keypoints Key points
- The take-home messages
- They will appear at the end of the tutorial
Useful literature
Further information, including links to documentation and original publications, regarding the tools, analysis techniques and the interpretation of results described in this tutorial can be found here.
